How to compare a cybersecurity package
Choosing the right cybersecurity package is a bit like picking the perfect home security system. You wouldn’t just slap a lock on the front door and call it a day, right? Similarly, safeguarding your business’s digital assets requires a comprehensive approach. Let’s walk through the key considerations to help you make an informed decision.
1. Comprehensive Features:
Start by evaluating what each cybersecurity package offers. A robust solution should go beyond basic antivirus protection. Look for features like:
- Conditional Access: Ensures only authorized users can access sensitive data.
- Email Security: Protects against phishing attacks and malicious attachments.
- Security Awareness Training: Empowers your team to recognize and avoid threats.
- Log Ingestion and Monitoring: Keeps tabs on system activities to detect anomalies.
- 24/7 Manned Security Operations Center (SOC): Provides round-the-clock vigilance against potential breaches.
Think of these features as the components of a high-tech security system for your business, each playing a vital role in keeping intruders at bay.
To help out with your comparison, we’ve done one of our own. Check it out
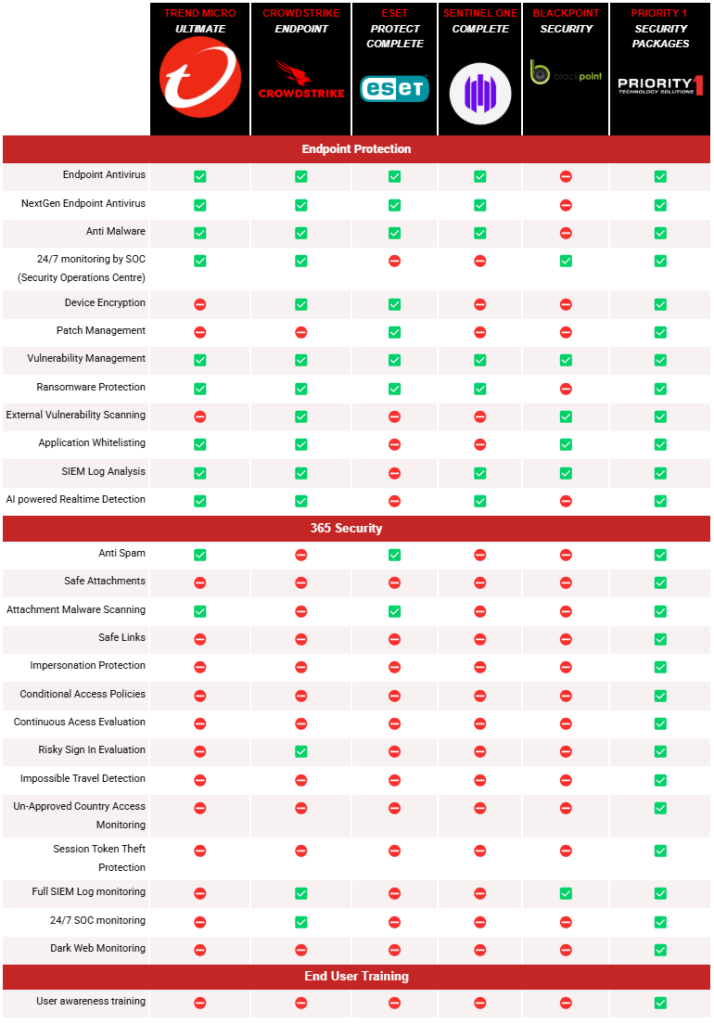
But why does our package cover so much that highly reputable solutions do not? It’s simple. We sell a “Package” not a “Product”. Many of our packages look something like this:
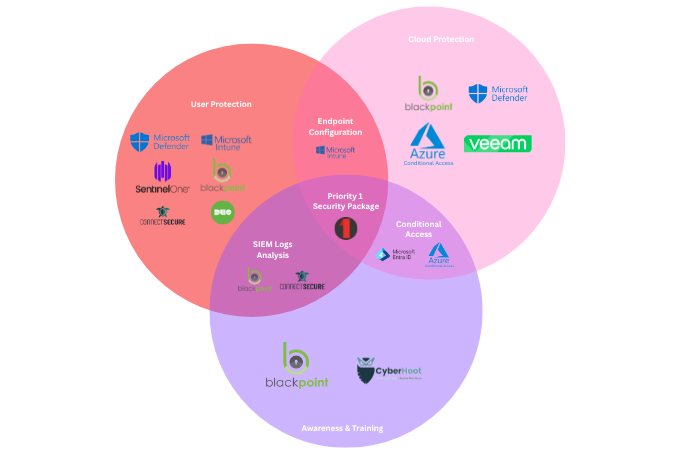
This probably means nothing to you, but it goes to show that you can’t just use one industry-leading product for cybersecurity. You need many industry-leading products working in harmony for security.
2. Supplier Reputability and Certifications:
Would you trust a locksmith without credentials? Similarly, the credibility of your cybersecurity provider matters. Check if they hold certifications like ISO/IEC 27001, an international standard for information security management. This certification demonstrates a commitment to maintaining rigorous security protocols and continuous improvement. Partnering with a certified provider gives you confidence that they’re not just talking the talk but walking the walk when it comes to protecting your data.
3. Pricing vs. Features:
Budget considerations are always in play, but remember, you often get what you pay for. Compare the features offered against the pricing structures. Sometimes, a slightly higher investment upfront can save you from costly breaches down the line. It’s about finding that sweet spot where cost meets comprehensive protection. Think of it as investing in a sturdy, reliable lock system rather than opting for a cheap one that a burglar could easily pick.
4. Red Flags – Overemphasis on Antivirus:
Be wary of providers who tout antivirus as the be-all and end-all of cybersecurity. While antivirus is a piece of the puzzle, it’s just that—a single piece. Cyber threats today are multifaceted, and a provider who doesn’t acknowledge this by offering a layered security approach might not be up to the task of fully protecting your business. It’s akin to relying solely on a guard dog without locking your doors and windows.
5. Beware of the extras
When evaluating cybersecurity packages, be cautious of providers who bundle in unrelated services, such as general IT support or non-security-related items. While bundling can sometimes offer convenience, it may also indicate that the provider is allocating fewer resources to critical security measures. This approach can dilute the effectiveness of the cybersecurity package, leaving your business vulnerable to threats. Ensure that the focus remains on comprehensive security features tailored to protect your digital assets.
In summary…
Selecting a cybersecurity package isn’t just about ticking boxes; it’s about ensuring a tailored fit for your organization’s unique needs. Take the time to assess potential providers thoroughly. After all, in the digital age, your business’s security is only as strong as the measures you put in place. Don’t settle for a one-size-fits-all solution—your business deserves a bespoke suit of armor.
Ready to fortify your digital defenses? Let’s discuss how we can customize a cybersecurity strategy that aligns perfectly with your business objectives.
